The Gmail Blue Checkmark issue has raised concerns among users regarding the authenticity of verified senders. In early June, a new method used by scammers to abuse the trust-based system was discovered. Despite the Blue Checkmark being intended to indicate messages from authenticated businesses and institutions, scammers found a way to manipulate this feature and display the checkmark on their statements. In this article, we will examine the factors that contributed to the failure, the tactics used by scammers to manipulate the system, and the steps taken to rectify this problem.

Email Authentication
Email has been a popular means of online communication for several decades. Over time, various systems have been developed to combat abuse and ensure secure transmission. One of the critical mechanisms in place is DMARC (Domain-based Message Authentication, Reporting, and Conformance). DMARC builds upon the Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) to prevent email spoofing and verify the authenticity of the sender’s name in the “from” field.
Gmail also employs VMC (Verified Mark Certificate) to indicate sender legitimacy. This digital attestation is based on legally trademarked information, helping establish brand identity. VMC is further utilized in BIMI (Brand Indicators for Message Identification), the system responsible for displaying a company’s icon alongside its messages in the Gmail inbox.
Authenticated emails from recognized organizations display the company logo and feature the blue “verified” checkmark when properly configured.
Uncovering the Gmail Blue Checkmark Issue
A cybersecurity engineer, Chris Plummer, noticed something amiss when he received emails in his Gmail inbox from suspicious-looking addresses. To his surprise, these emails included the company’s logo and the Blue Checkmark. Examining the example shared below, we can see that although the message appears to be from a UPS.com account, the presence of a gibberish subdomain and an unusual account suggests spoofing.
Deal of the Day
Anker 737 Power Bank Now Available for $74: Cyber Monday Deal
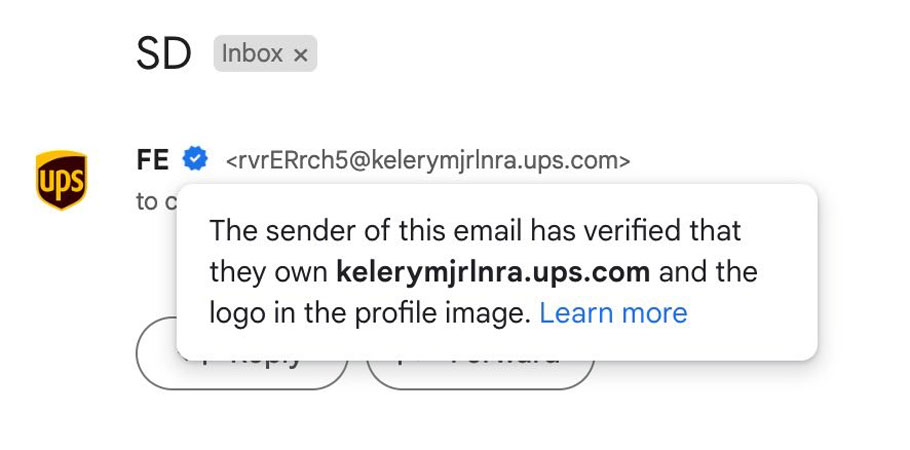
Upon investigating the matter, Google disclosed that the issue is “a third-party security vulnerability allowing bad actors to appear more trustworthy than they are.” The crux of the problem lies in the coexistence of SPF and DKIM authentication methods and how BIMI handles cases where one pass but the other fails.
Since UPS trusted Microsoft to send emails on its behalf, when Gmail received a message from a scammer through a Microsoft server, it considered it a legitimate UPS email that complied with BIMI standards. This occurred despite the presence of a spoofed subdomain. Gmail did not delve deeper into the chain of email systems the message passed through or whether it failed any prior validation attempts. The Blue Checkmark would appear if the most recent test looked good.
Solutions for Gmail Blue Checkmark Issue
The Gmail Blue Checkmark issue raises concerns about the average email user’s ability to discern the authenticity of a sender. Should users abandon trust in email altogether? Assume that every message could be fake. Fortunately, measures are already being taken to address this problem.
One notable action taken was UPS removing Outlook as an authorized mail server in its SPF record. This adjustment prevented this specific attack.
When issues like this arise, it is crucial for all parties involved to resist the temptation of adopting a “my part works, the problem must be your part” attitude. Even now, the group responsible for BIMI appears somewhat dismissive, claiming that the incident merely highlights a long-standing issue with SPF, predating BIMI and DMARC. It is essential for the involved parties to proactively resolve known problems rather than waiting for hackers to exploit them. Only then can we have confidence in our trust in online communications?
FAQs
Can scammers still send spoofed emails without the Blue Checkmark?
Yes, scammers can still send spoofed emails without the Blue Checkmark. The Blue Checkmark is to provide an additional layer of verification for business authentication and institutions, but scammers found ways to bypass it.
What steps can I take to safeguard myself from becoming a victim of email scams?
To safeguard yourself against email scams, exercise caution while opening emails from unfamiliar senders or those with dubious addresses. Refrain from clicking on suspicious links or downloading attachments from such emails. Verify the sender’s credibility through alternative methods, such as contacting the company directly.
Are other email providers vulnerable to similar issues?
While the Gmail Blue Checkmark issue was specific to Gmail’s implementation of BIMI, other email providers may face similar challenges. Email authentication systems are continuously evolving to mitigate risks and enhance security.
How can businesses ensure their emails appropriately have Authentication?
Businesses can implement robust email authentication measures by correctly configuring DMARC, SPF, and DKIM. Monitoring and updating these settings is essential to maintaining a secure email environment.
Will the Gmail Blue Checkmark issue be fully resolved in the future?
The Gmail Blue Checkmark issue has prompted discussions and actions within the email community to address the vulnerability. Email authentication systems are evolving, and companies fixing the vulnerabilities are patched. Such problems are expected to be mitigated.
Wrap Up
The Gmail Blue Checkmark issue exposed a vulnerability in the system that scammers exploited to appear as verified senders. We can understand the complexity of email authentication from the interplay between DMARC, SPF, DKIM, VMC, and BIMI. Actions are currently being taken to tackle this problem and guarantee that email recipients can have confidence in the authenticity of Senders. By implementing proactive strategies and addressing identified weaknesses, we can uphold the integrity of online communication.

Selva Ganesh is the Chief Editor of this Blog. He is a Computer Science Engineer, An experienced Android Developer, Professional Blogger with 8+ years in the field. He completed courses about Google News Initiative. He runs Android Infotech which offers Problem Solving Articles around the globe.



Leave a Reply