LastPass, a popular password manager, has been hit by two data breaches in the past year that compromised the personal data of millions of users. The company recently revealed that a single employee, whose home computer was compromised by keylogging malware, caused both breaches. Although the details of the second breach were recently announced, it turns out that the same employee played a significant role in both incidents.

Recent LastPass Data Breach
LastPass discovered the first breach in August 2022 when the hackers accessed the company’s systems using information obtained from the compromised employee’s computer. The second breach occurred in November of the same year when the hackers used the same employee’s computer to access LastPass systems and steal partially encrypted user login data.
Reports indicate that a keylogger was installed on the personal computer of an individual in a senior engineering position at LastPass via an exploit found in Plex, a service used for personal cloud-based storage and streaming of movies. The keylogger was then used to gain access to corporate-level caches and compromise sensitive user data.
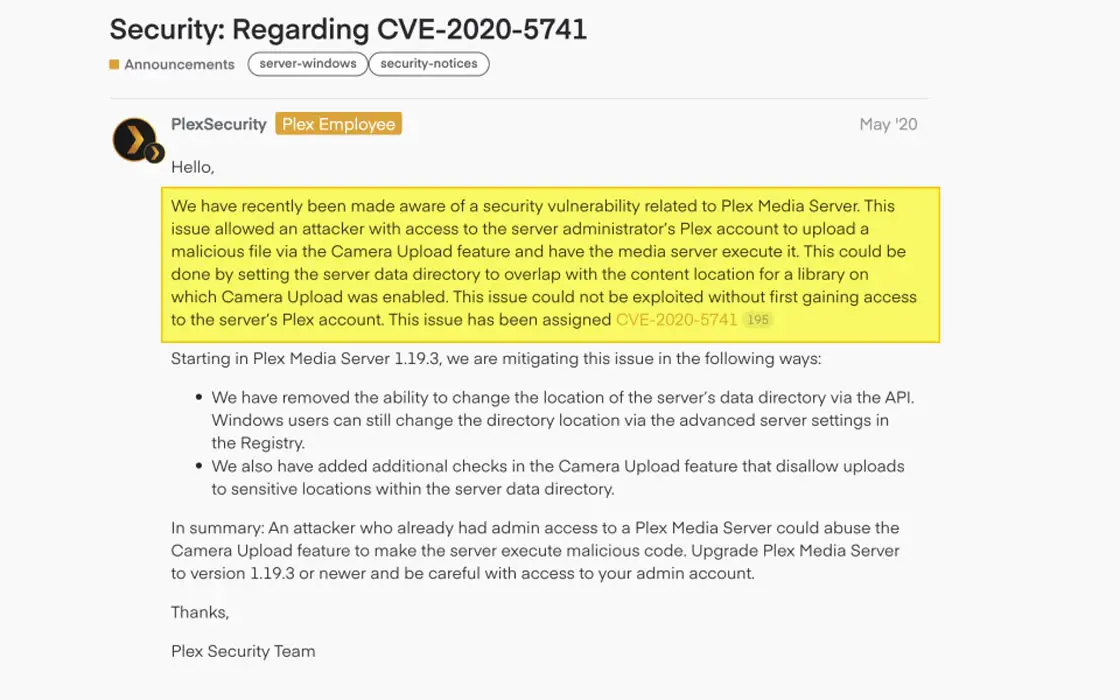
Subsequently, they disclosed that the exploit in question leveraged a vulnerability made public on May 7, 2020. As a result, anyone with access to a server administrator’s Plex account could upload a malicious file through the Camera Upload feature and execute it on the media server. For some reason, the LastPass employee failed to update their client to apply the patch released to fix the loophole.
Deal of the Day
Anker 737 Power Bank Now Available for $74: Cyber Monday Deal
Fix for LastPass Data Breach Issue
LastPass released an updated version of Plex Media Server on the same day to patch the gap. However, the version that addressed the exploit was around 75 versions ago, highlighting the importance of keeping software up-to-date.
LastPass declined to comment on the issue, leaving users concerned about the security practices followed by the company.
In a time when data breach is becoming more frequent, companies need to take proactive measures to safeguard user data. As a user, it is equally important to stay vigilant of potential risks and take necessary steps to protect personal information.
Some valuable tips to Stay Protected from Data Breach
Remember, since your data is already online. We can avoid access or avoid easy access using the tips below.
Create strong and unique passwords for all your online accounts
Consider generating strong and unique passwords for each online account to reduce the risk of compromise. Reusing passwords across multiple accounts increases the risk of all your accounts.
Enable two-factor authentication (2FA) wherever possible
Two-factor authentication (2FA) enhances your security by requiring you to enter a code sent to your phone or email in addition to your password.
Keep your software up-to-date
Software updates often include security patches that fix vulnerabilities that hackers can exploit.
Be cautious of phishing scams
Be careful of phishing scams, fraudulent emails, or messages that deceive you into sharing your personal information. It would be best to be cautious when clicking links or downloading attachments from unknown sources.
Use reputable antivirus software
Antivirus software can detect and remove malware that could compromise your computer and steal your personal information.
FAQs
What happened with LastPass recently?
LastPass experienced two massive data breaches last year, which caused the company to lose its reputation as one of the top password managers.
How did the second data breach happen?
A malevolent actor was responsible for the second data breach, installing a keylogger onto a senior engineer’s home computer via an exploit in Plex, a personal cloud service for movie storage and streaming. As a result, the perpetrator could gain access to corporate-level caches.
Did the LastPass employee participate in the second data breach?
The LastPass engineer played a significant role in the security breach. The exploit to access the system took advantage of a vulnerability disclosed on May 7, 2020. Unfortunately, the employee did not update their client to apply the patch, leaving the system vulnerable to attack.
Why didn’t the LastPass employee update their Plex Media Server?
The cause of why the employee did not update their Plex Media Server is currently unknown. According to PCMag, Plex stated that they provide notifications through the admin UI about available updates and will even perform automatic updates in certain situations.
What did LastPass do in response to the data breach?
The attacker took advantage of a vulnerability, which the company confirmed—a vulnerability in a previous version of Plex Media Server that didn’t fix by a patch. A LastPass DevOps engineer owned the computer where this vulnerability was present. LastPass declined to comment on the new information about the engineer’s role in the second data breach.
Wrap Up
To sum up, the recent data breach in LastPass is a reminder of cybersecurity’s significance. Users must recognize the potential risks and implement measures to safeguard their data. For companies, it is imperative to prioritize security and take proactive steps to protect user data.
Stay safe online, and always remember to be vigilant!

Selva Ganesh is the Chief Editor of this Blog. He is a Computer Science Engineer, An experienced Android Developer, Professional Blogger with 8+ years in the field. He completed courses about Google News Initiative. He runs Android Infotech which offers Problem Solving Articles around the globe.



Leave a Reply